Audit logs
Audit logs show security-relevant operations a user has processed. For example, an audit log is generated when a user logs into a gateway.
Requirements
ROLES & PERMISSIONS:
- To view audit logs: READ permission for permission type “Audit”
- To create audit logs you need Admin permission for the permission type “Audit”. Note however, that you cannot create audit logs from the UI. For details on how to create audit logs via REST refer to Audits in the Cumulocity IoT OpenAPI Specification.
To view audit logs
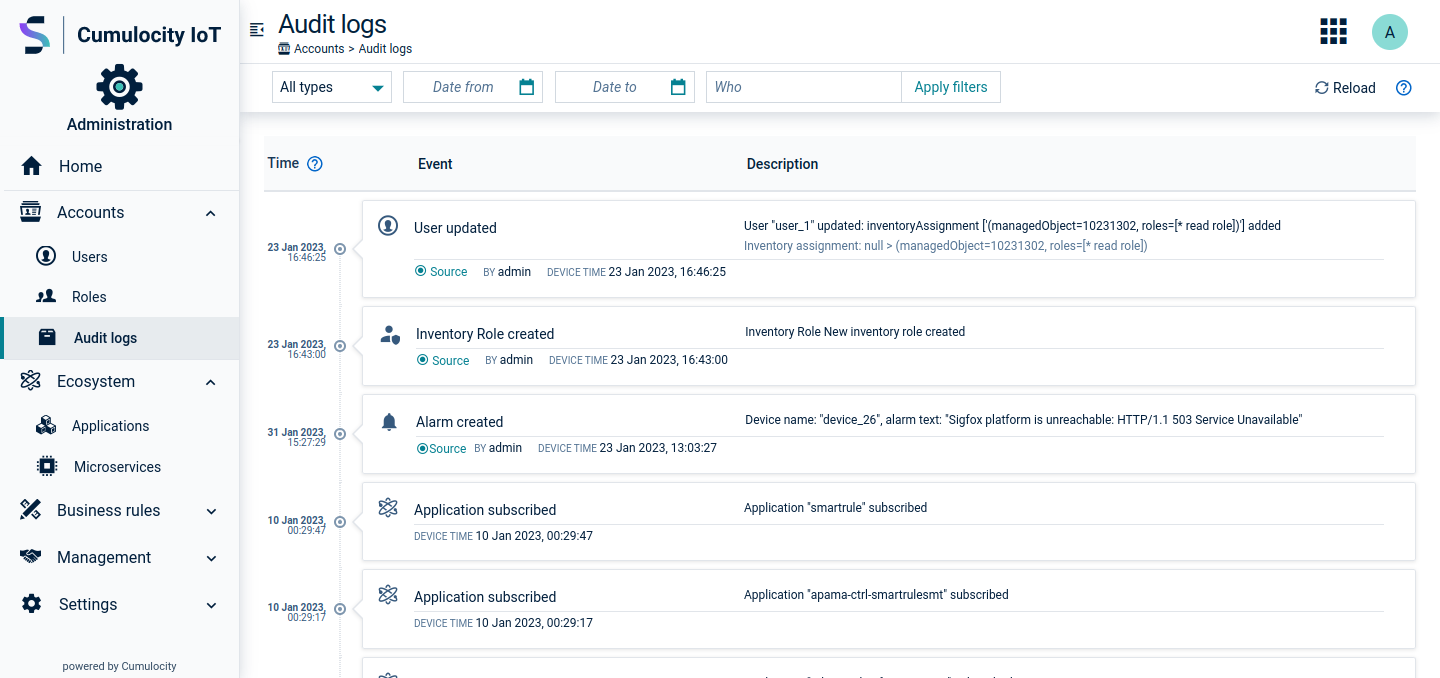
To view the audit log list, click Audit logs in the Accounts menu. For each log entry, the following information is provided:
| Column | Description |
|---|---|
| Server time | Server time when the operation was processed. |
| Event | Type of operation, for example "Alarm created", "Smart rule deleted". Below it, the user who processed it is displayed. |
| Description | Provides further information depending on the operation, for example, the device name, alarm text, operation status. |
| Device time | Device time when the operation was processed. This can differ from the server time. |
Only the last 100 logs are visible. Scroll down the page to Load more to view more log entries.
Info
The audit log list is not automatically refreshed after a realtime update for operations. Click Reload at the right of the top menu bar to update the list to the latest operations.
To filter logs
In order to easily search through logs, you can filter logs by:
- Type (alarm, operation, smart rule, and so on)
- Device time (provide a date range in “From” and/or “To” inputs)
- User
To apply a filter, click the Apply button next to the respective filter field. To discard filters, click the clear icon next to the Apply button (only visible if filters are set).
Audit log types
| Audit type | Actions |
|---|---|
| Alarm |
|
| Application |
|
| Bulk operation |
|
| Data broker connector |
|
| Devices availability monitoring |
|
| Global role |
|
| Inventory |
|
| Inventory role |
|
| Operation |
|
| Option |
|
| Reliable notification |
|
| Report |
|
| Single sign-on |
|
| Smart rule |
|
| Tenant |
|
| Tenant auth configuration |
|
| Trusted certificate |
|
| User |
|
| User login |
|
Info
See also Audit logs for Streaming Analytics.
